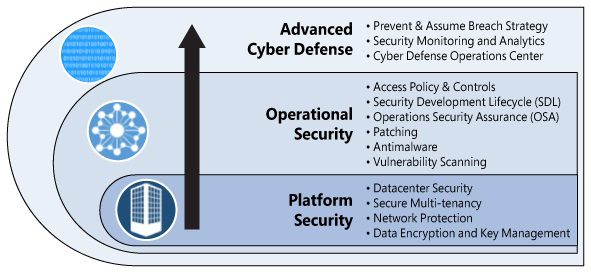
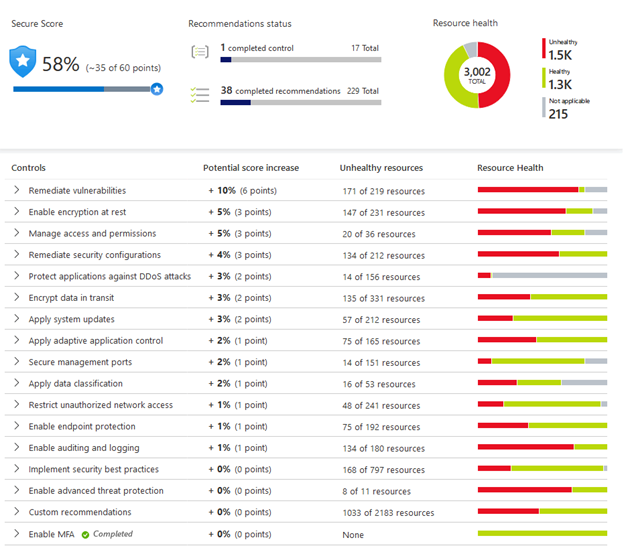
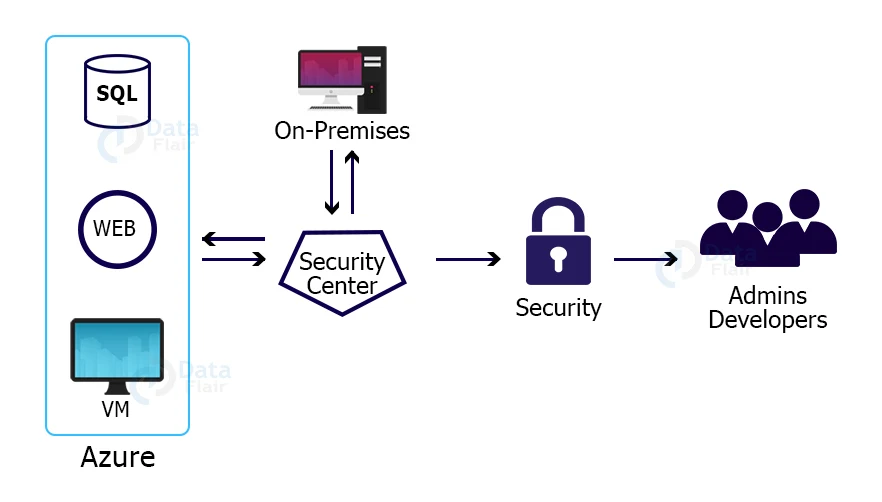
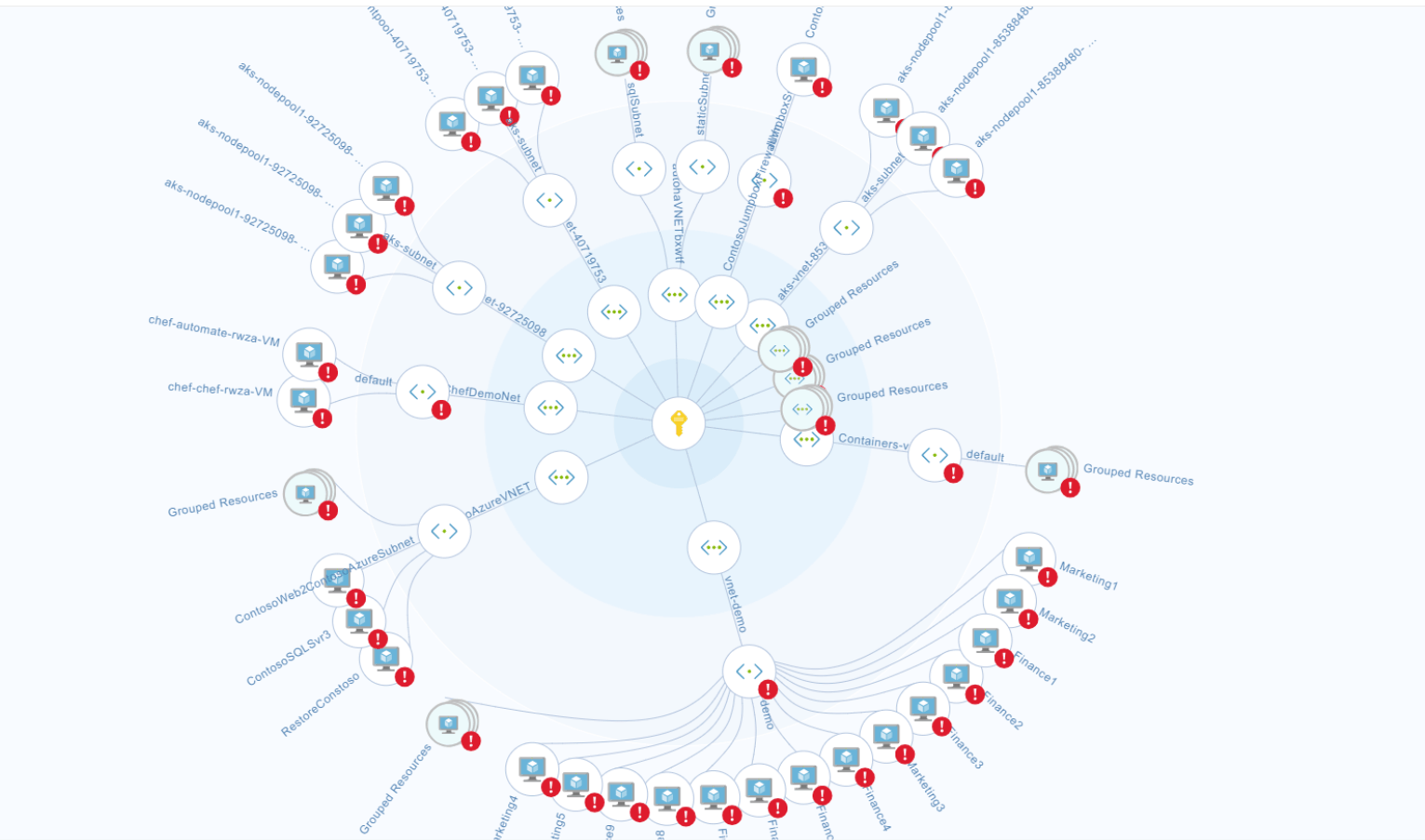
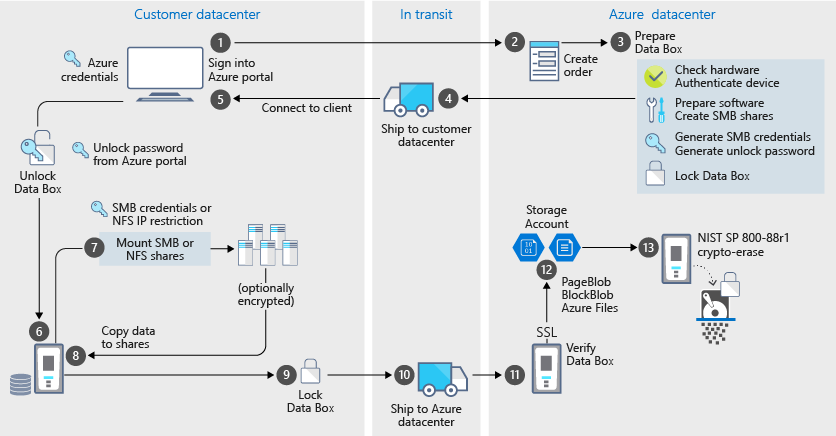
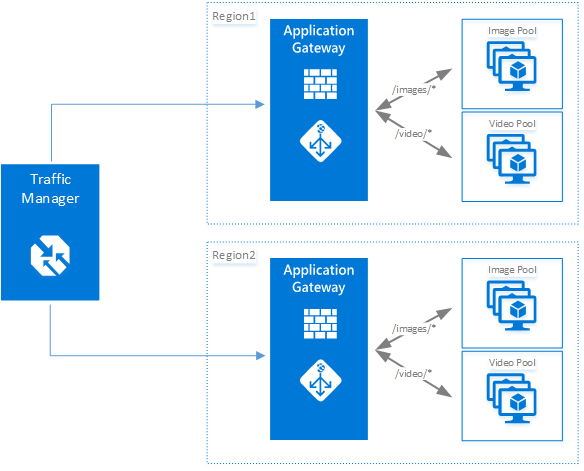
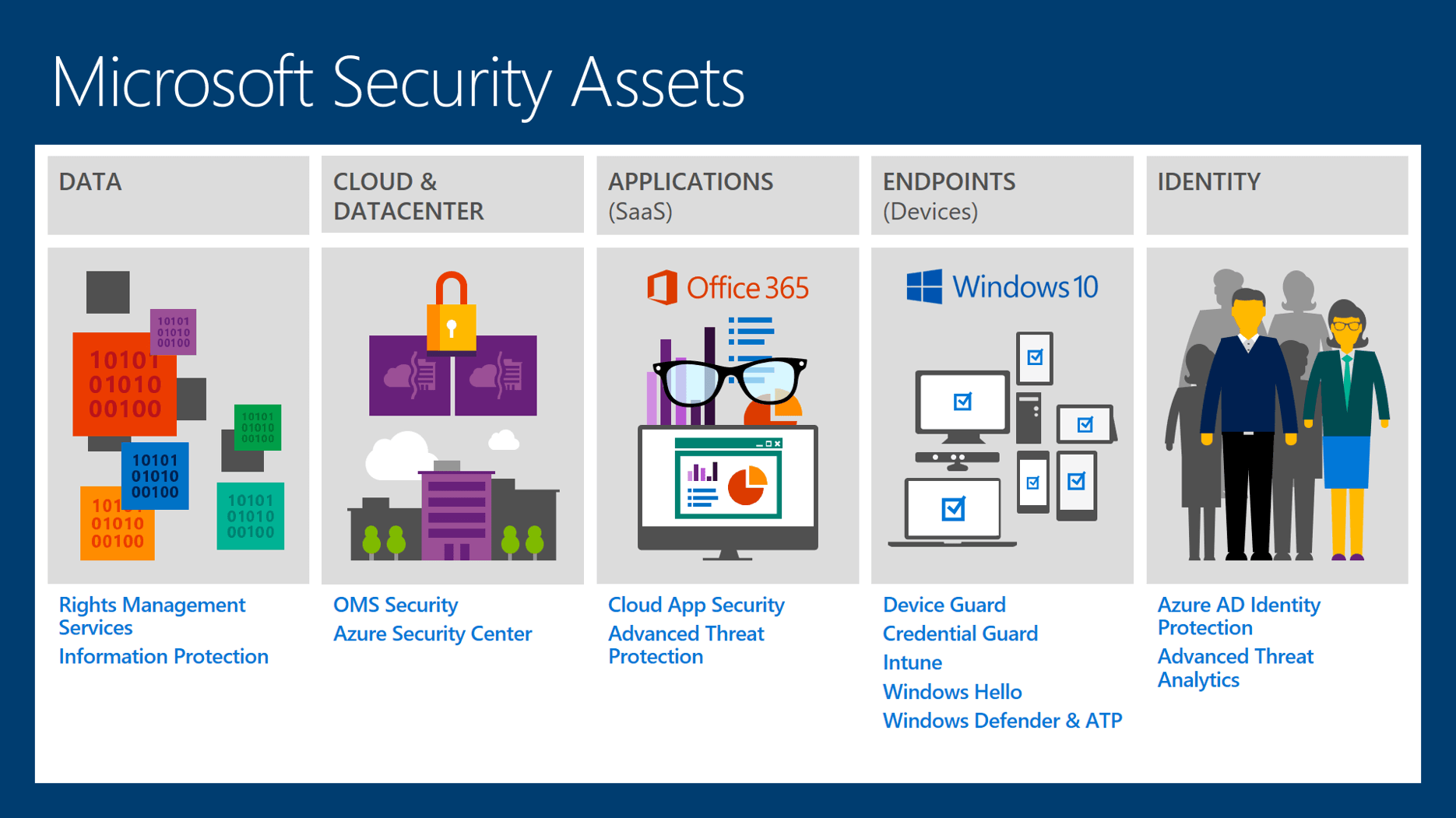
Microsoft may be all-in on cloud computing, but Azure reliability is lagging the competition – GeekWire

Microsoft Designing Open Source Data Center Security Chip | Data Center Knowledge | News and analysis for the data center industry

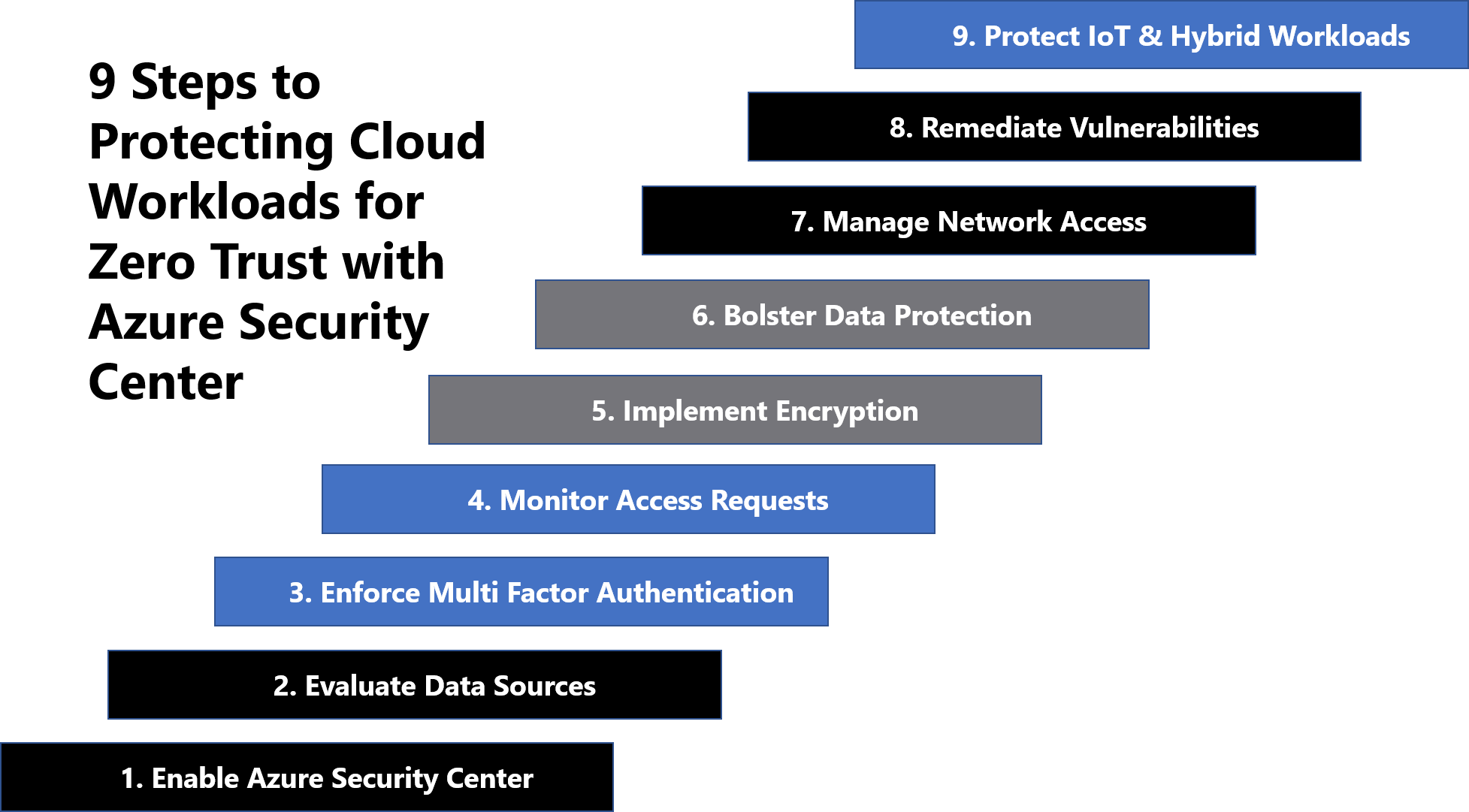
What is the difference between Azure Security Center and Azure Sentinel? | by John Yoon | The Cloud Builders Guild | Medium