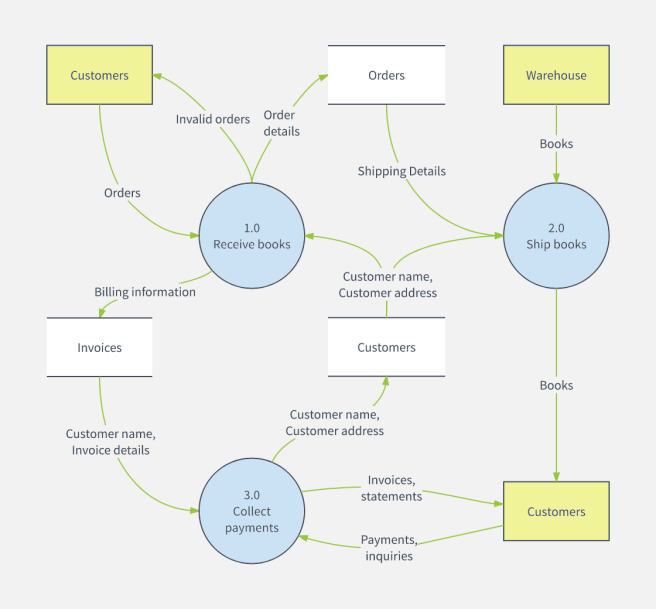
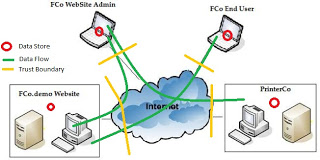
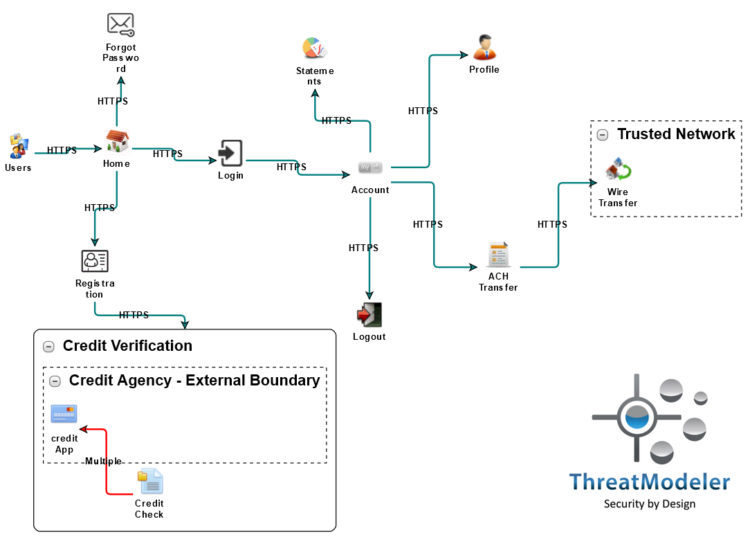
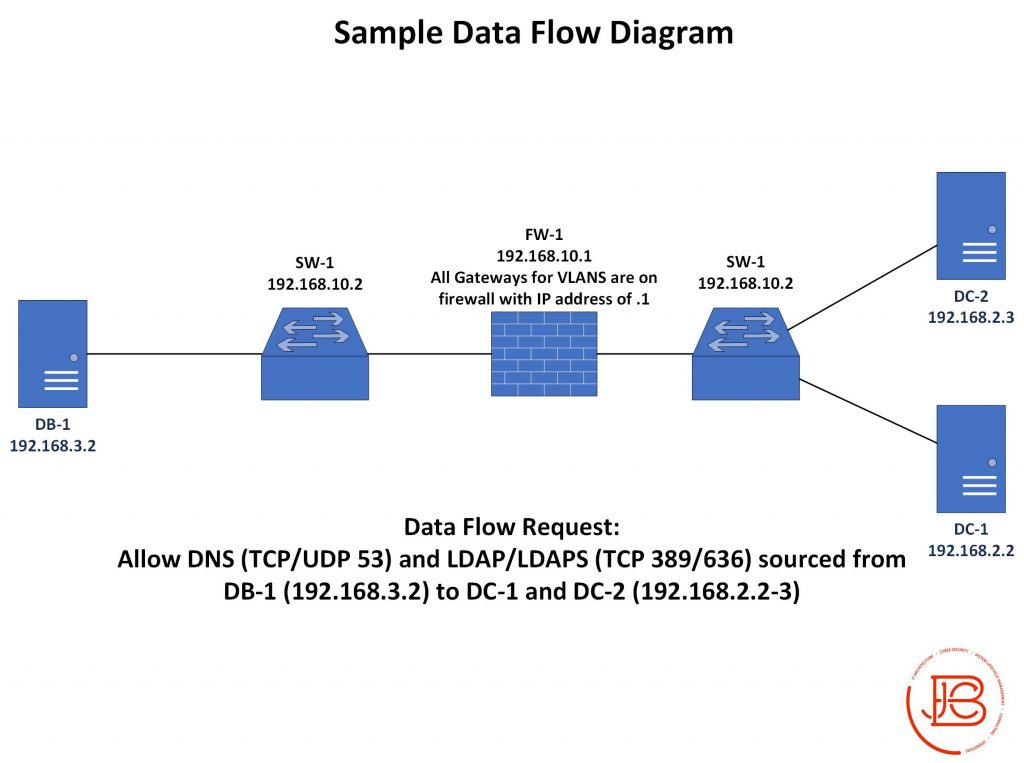
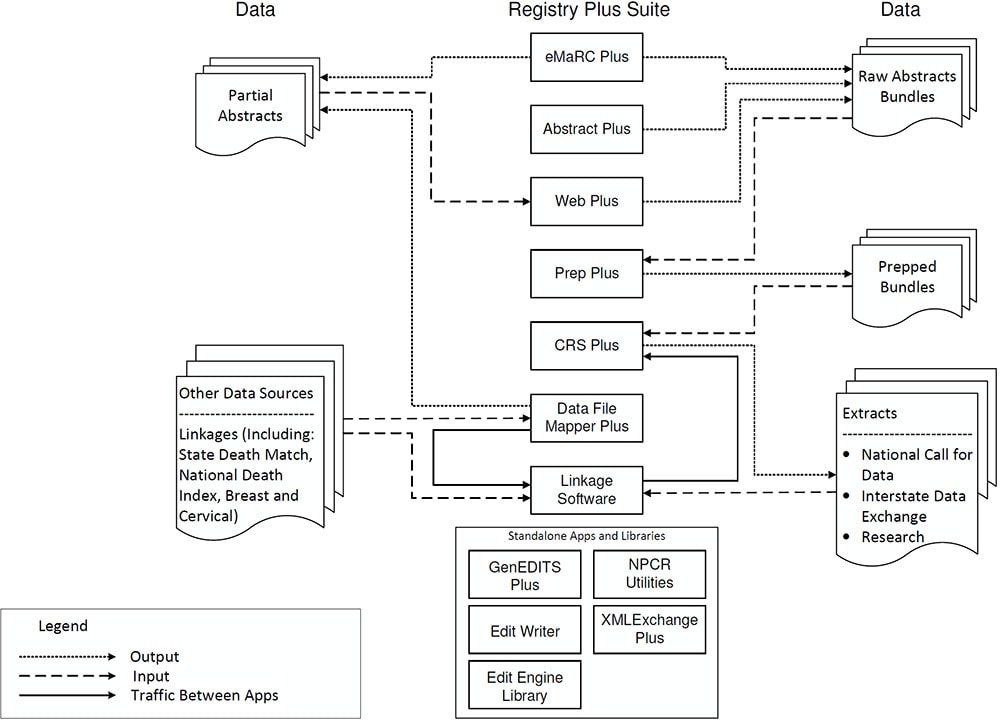
Data flow diagram showing how data from various sources flows through... | Download Scientific Diagram

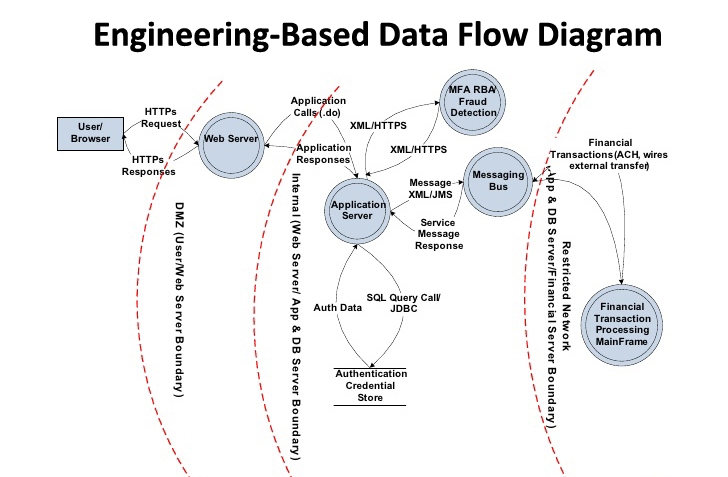
SECURITY IN THE DESIGN PHASE. Security is important in every stage of… | by WORTH Internet Systems | Medium
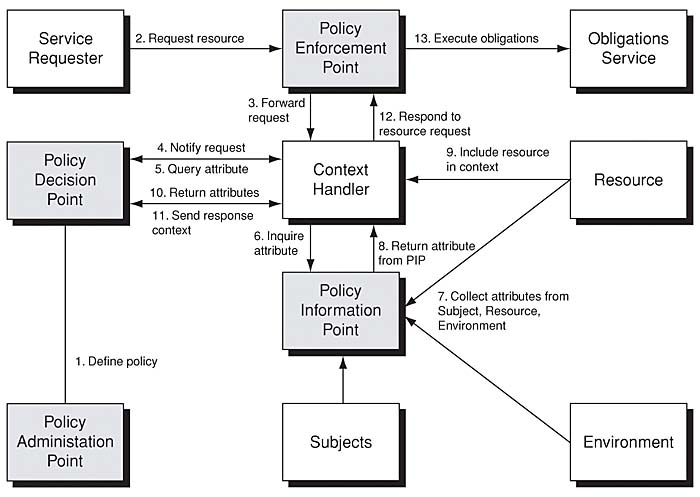
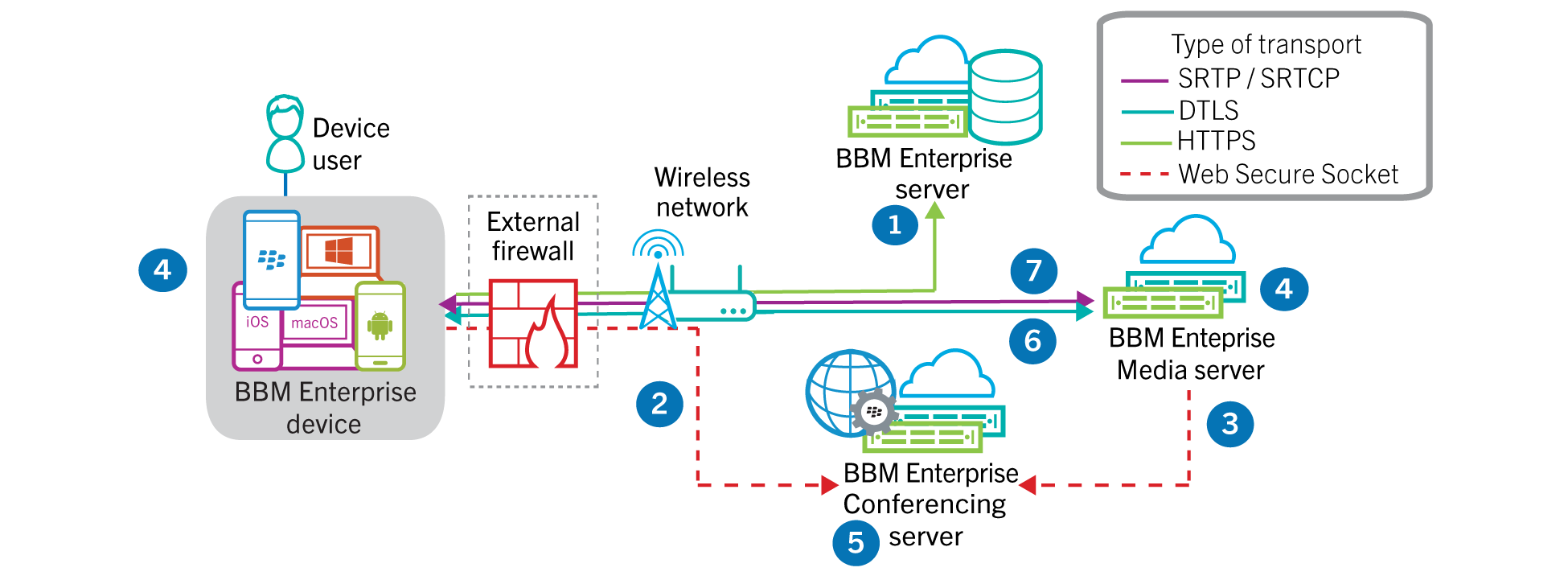
XACML Data Flow and Architecture | Core Security Patterns: Identity Management Standards and Technologies | InformIT