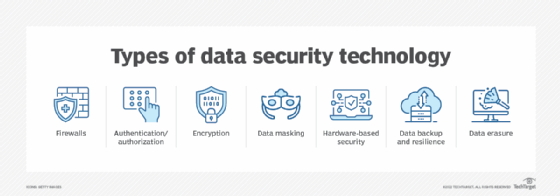
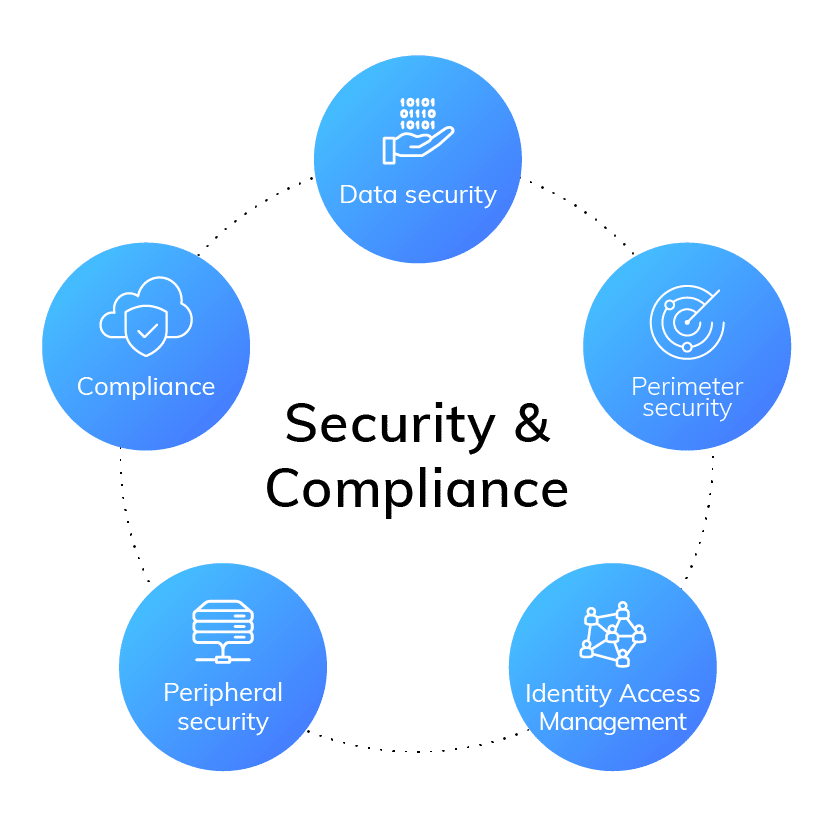
Official PCI Security Standards Council Site - Verify PCI Compliance, Download Data Security and Credit Card Security Standards

Data Security Compliance: A Cheat Sheet for IT | Data security, Home security systems, Wireless home security systems








![Data Compliance: What You Need to Know [2022] | Hyperproof Data Compliance: What You Need to Know [2022] | Hyperproof](https://hyperproof.io/wp-content/uploads/2021/02/what-is-data-compliance-1024x1024.jpg)