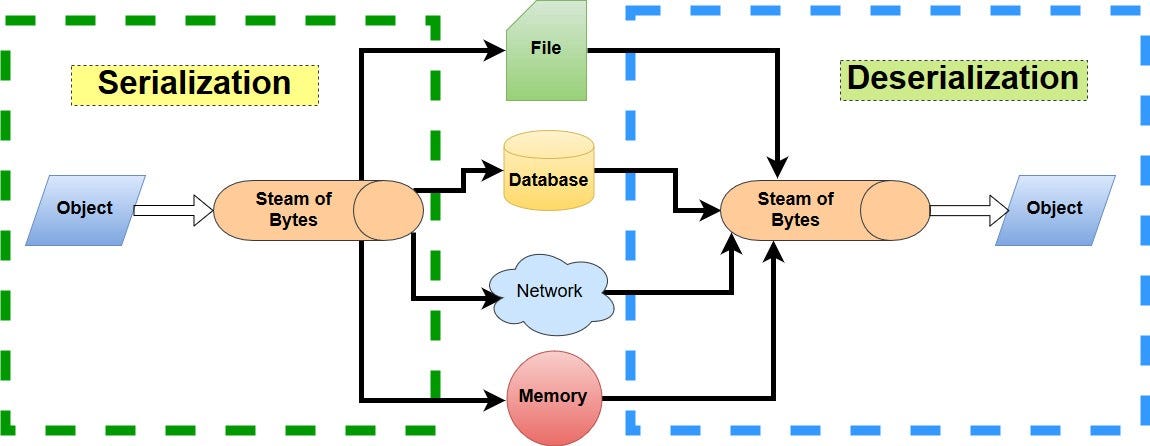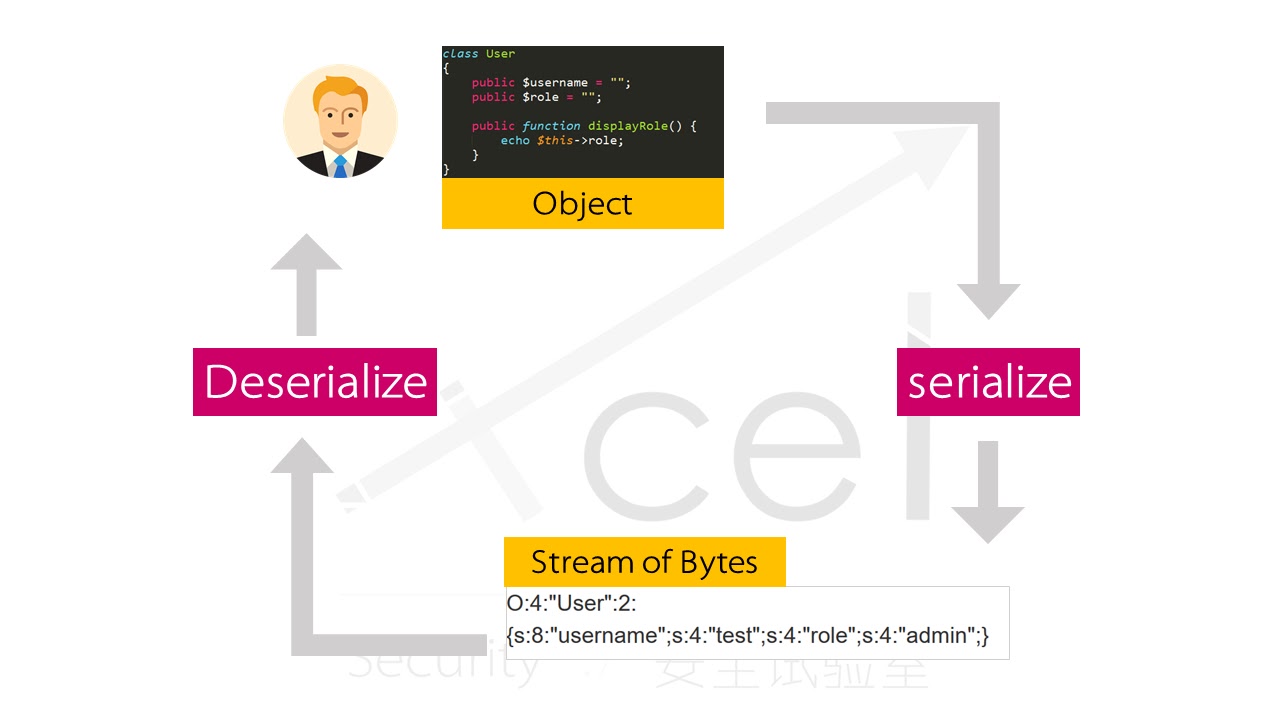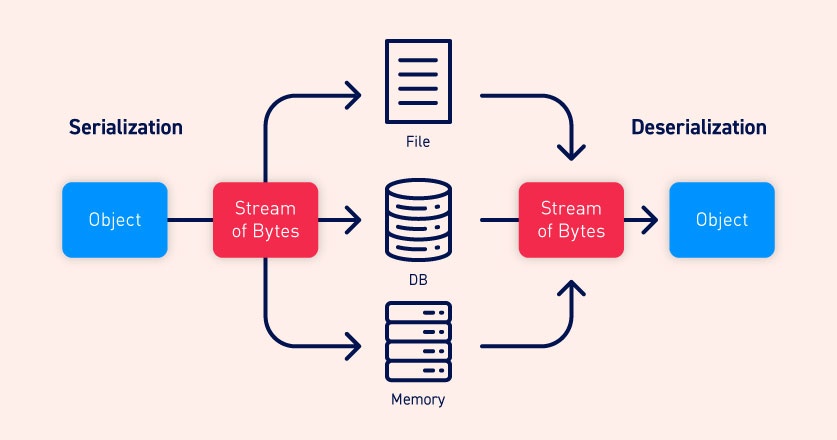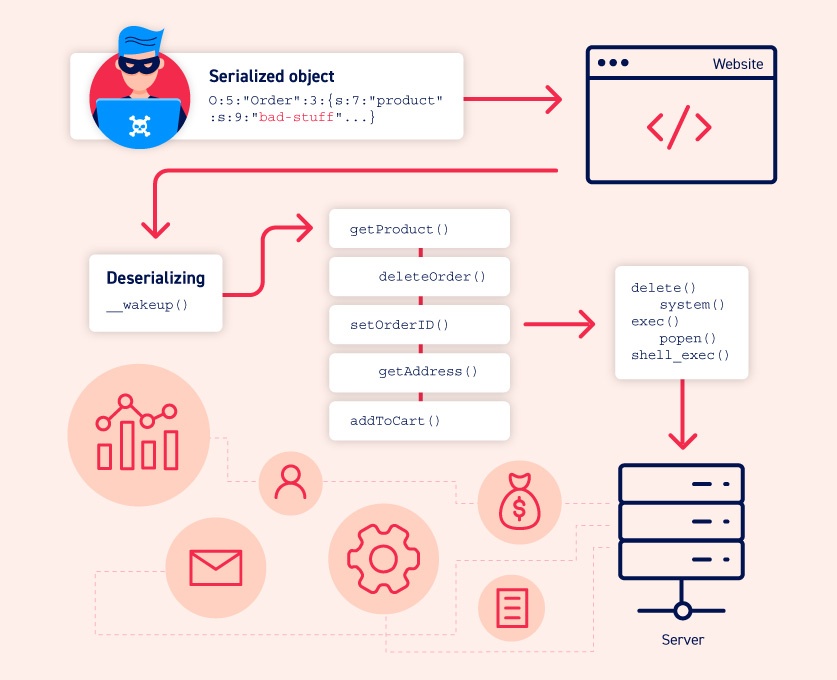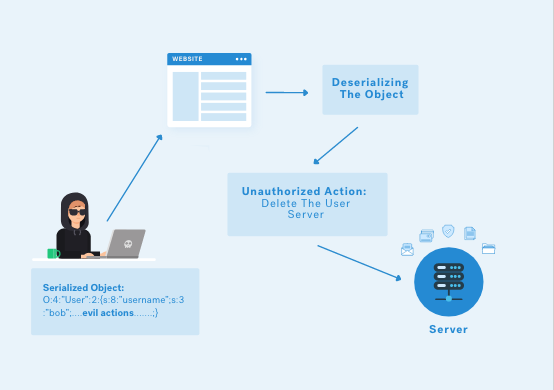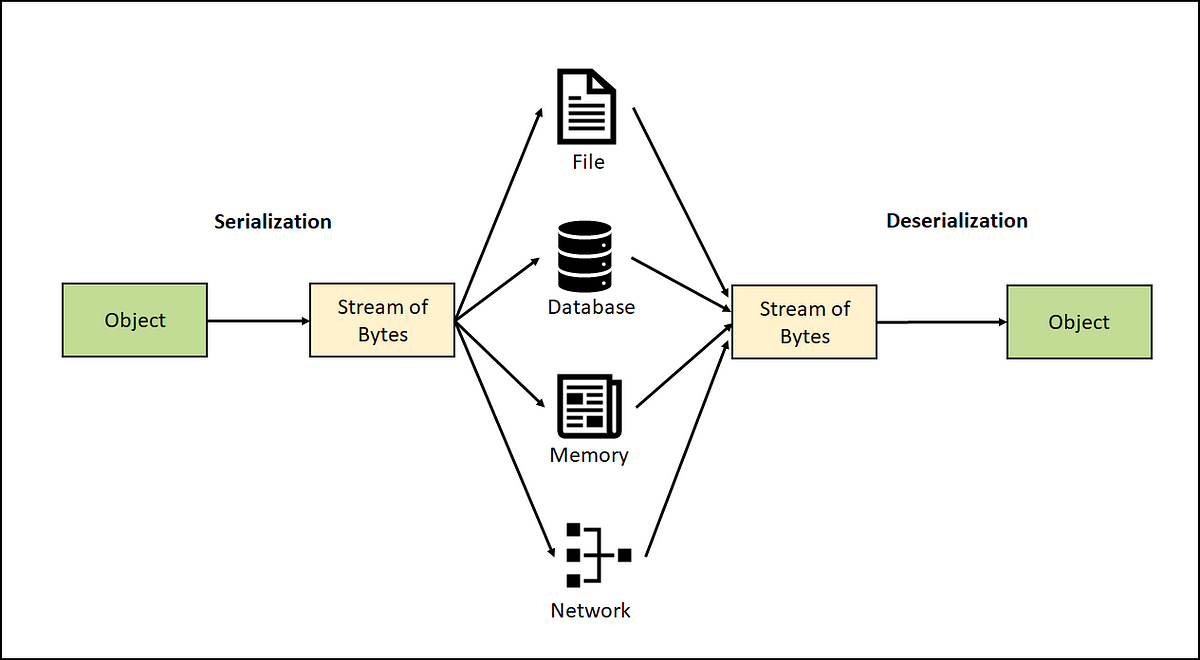
Serialization Filtering — Deserialization Vulnerability Protection in Java | by Albin Issac | Tech Learnings | Medium
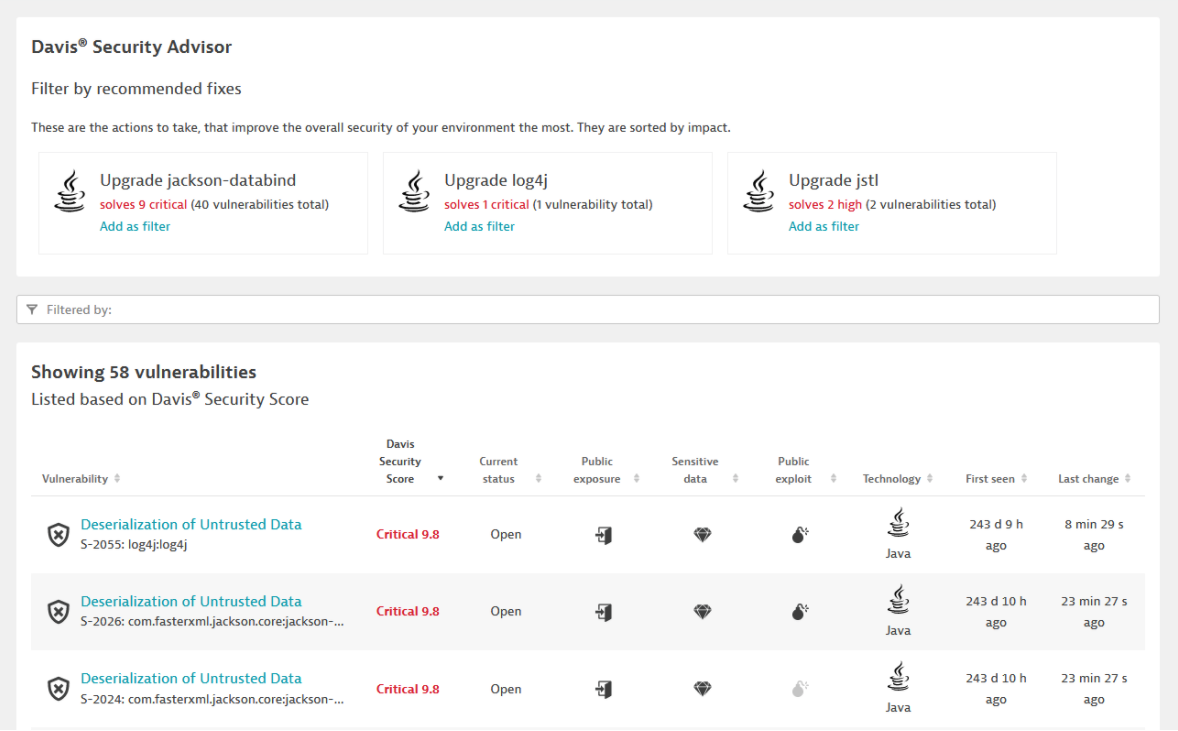
Dealing with Deserialization of Untrusted Data in Java Applications - GBHackers - Latest Cyber Security News | Hacker News

Checkmarx Research: Apache Dubbo 2.7.3 – Unauthenticated RCE via Deserialization of Untrusted Data (CVE-2019-17564) | Checkmarx.com
Dealing with Deserialization of Untrusted Data in Java Applications - GBHackers - Latest Cyber Security News | Hacker News